Dark Web Monitoring
Gain deep visibility into hidden dark web channels where cybercriminals trade sensitive information. With cDFN WatchTower’s monitoring, identify risks to your organization—like exposed credentials and unauthorized brand mentions—and take immediate action to secure your data. Real-time alerts and advanced threat analysis enable precise threat mitigation, helping you reduce potential damage and strengthen your security posture with confidence.
Gain deep visibility into hidden dark web channels where cybercriminals trade sensitive information. With cDFN WatchTower’s monitoring, identify risks to your organization—like exposed credentials and unauthorized brand mentions—and take immediate action to secure your data. Real-time alerts and advanced threat analysis enable precise threat mitigation, helping you reduce potential damage and strengthen your security posture with confidence.
Gain deep visibility into hidden dark web channels where cybercriminals trade sensitive information. With cDFN WatchTower’s monitoring, identify risks to your organization—like exposed credentials and unauthorized brand mentions—and take immediate action to secure your data. Real-time alerts and advanced threat analysis enable precise threat mitigation, helping you reduce potential damage and strengthen your security posture with confidence.
Dark Web Monitoring
Dark Web Monitoring
Dark Web Monitoring for Proactive Cyber Defense
Dark Web Monitoring for Proactive Cyber Defense
Dark Web Monitoring for Proactive Cyber Defense
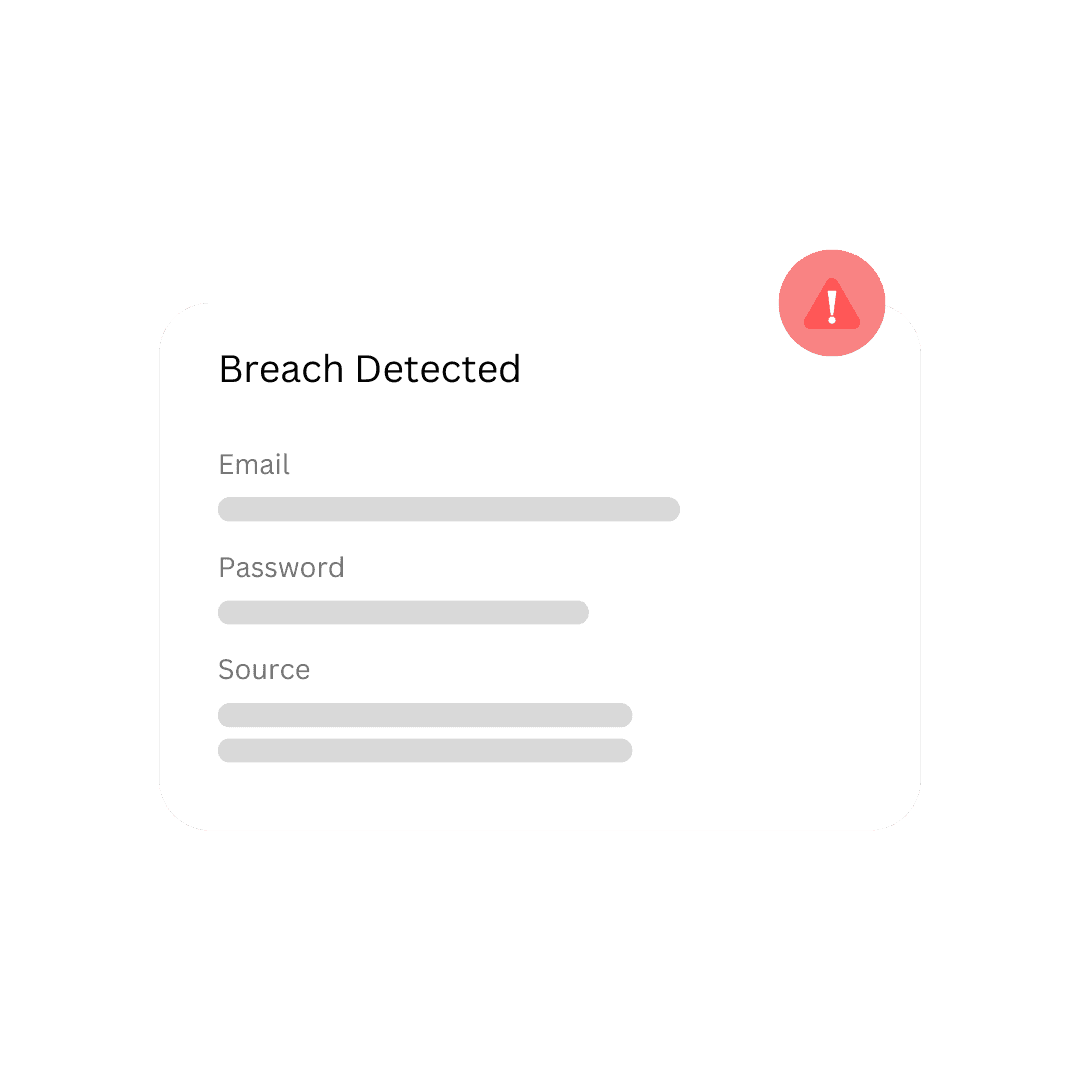


Third-Party Breaches
Third-Party Breaches
Third-Party Breaches
Detect breaches impacting third-party vendors, helping you understand potential risks originating outside your organization.
Detect breaches impacting third-party vendors, helping you understand potential risks originating outside your organization.
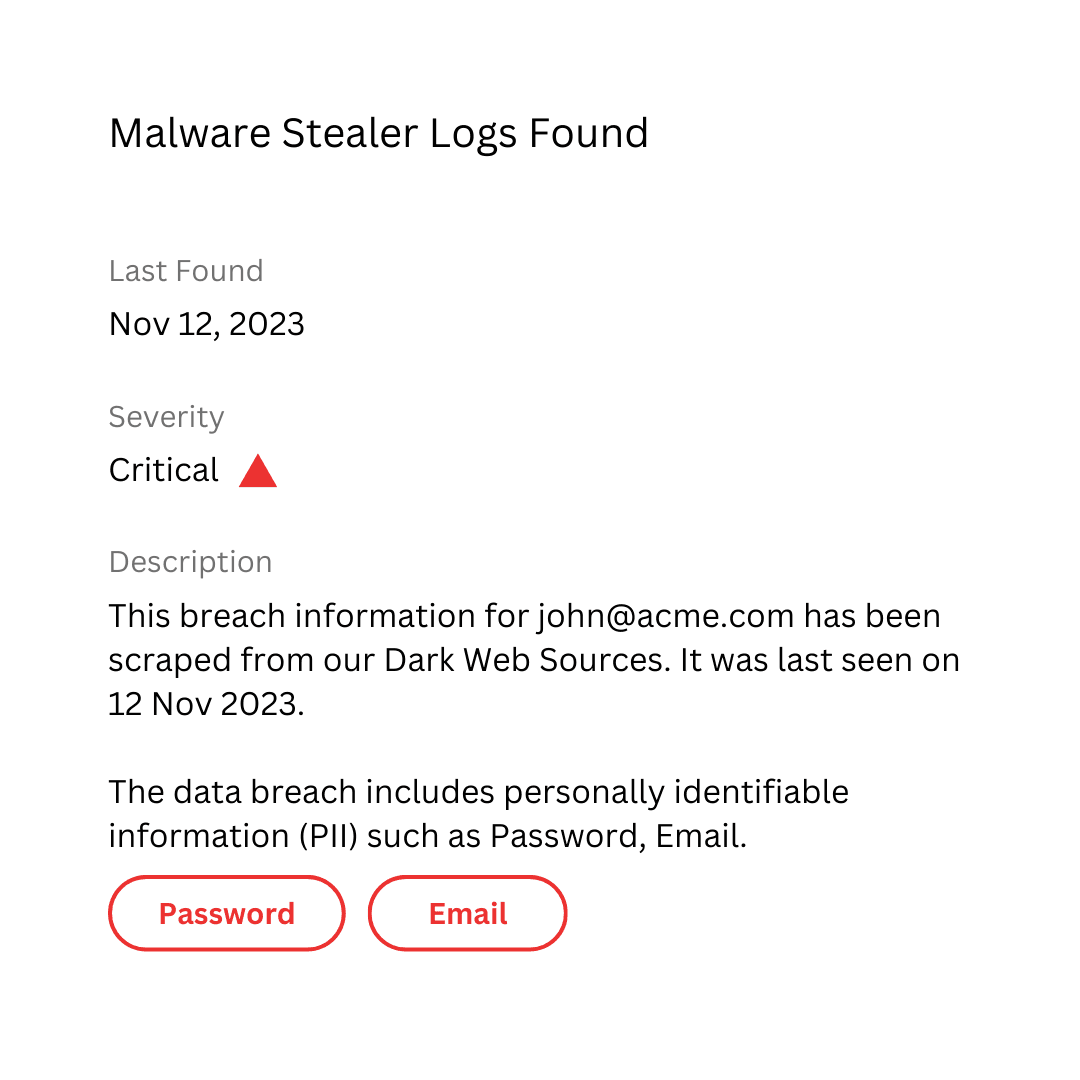


Malware Stealer Logs
Malware Stealer Logs
Malware Stealer Logs
Identify credentials and personal information captured by malware stealer logs before they’re exploited.
Identify credentials and personal information captured by malware stealer logs before they’re exploited.
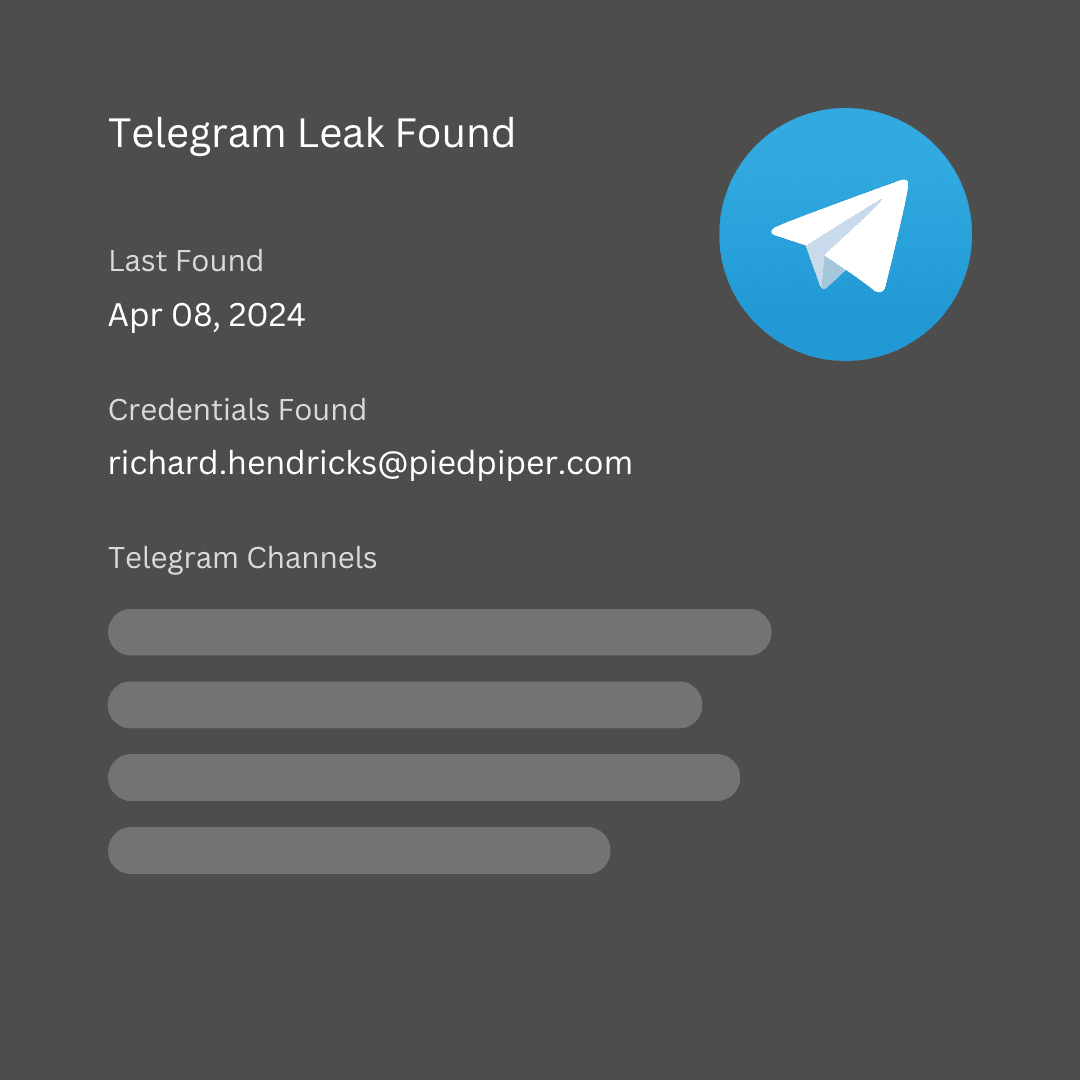


Telegram Leaks
Telegram Leaks
Telegram Leaks
Monitor Telegram channels for sensitive data leaks involving your organization.
Monitor Telegram channels for sensitive data leaks involving your organization.
Risk and Exposure Insights
Risk and Exposure Insights
Risk and Exposure Insights
Real-Time Alerts for Immediate Action
Gain real-time insights into cyber threats emerging across dark web marketplaces, forums, and encrypted messaging channels. With timely alerts, your team is equipped to respond to risks as soon as they surface, strengthening your overall threat intelligence.
Gain real-time insights into cyber threats emerging across dark web marketplaces, forums, and encrypted messaging channels. With timely alerts, your team is equipped to respond to risks as soon as they surface, strengthening your overall threat intelligence.
Customizable Monitoring Scope for Tailored Protection
Tailor your monitoring scope to focus on your organization's most important assets, such as corporate domains, intellectual property, executives, subsidiaries, or partner brands.
Tailor your monitoring scope to focus on your organization's most important assets, such as corporate domains, intellectual property, executives, subsidiaries, or partner brands.
Ransomware Risk Score
Our proprietary Ransomware Risk Score evaluates dark web findings to determine the likelihood of a ransomware attack. By considering factors like exposed credentials, open vulnerabilities, and industry-specific risks, this score helps you understand which threats need immediate attention.
Our proprietary Ransomware Risk Score evaluates dark web findings to determine the likelihood of a ransomware attack. By considering factors like exposed credentials, open vulnerabilities, and industry-specific risks, this score helps you understand which threats need immediate attention.
Comprehensive Coverage of Dark Web Sources
cDFN WatchTower collects data from an extensive range of dark web channels, including underground forums, stealer logs, and encrypted Telegram channels where cybercriminals often exchange information.
cDFN WatchTower collects data from an extensive range of dark web channels, including underground forums, stealer logs, and encrypted Telegram channels where cybercriminals often exchange information.



Secure Your Organization with Real-Time Dark Web Monitoring
Secure Your Organization with Real-Time Dark Web Monitoring
Secure Your Organization with Real-Time Dark Web Monitoring
Discover potential threats, take proactive action, and protect your assets from data leaks and unauthorized access.
Discover potential threats, take proactive action, and protect your assets from data leaks and unauthorized access.